As soon as you have an email address, you’re going to start getting phishing attacks. Phishing attacks are super easy to perform, very low cost, and can run continuously. That’s why they’re a favorite of people who are trying to get into your company. The simple, secure solution to phishing attacks is two-factor authentication. It’s so important to have two-factor authentication that Backstop will continuously verify your company for free. Forever. Sign up here if you don’t already have an account.
The goal of a phishing attack is to get someone in your company to give up their username and password to an important system they use. It can be anything from access to their email account, all the way to bank accounts, credit cards, and other high value targets.
Attackers get this information by sending you to a fake domain, that looks like the real thing. For example, one of your employees receives an email that looks like this (image courtesy of phishing.org):
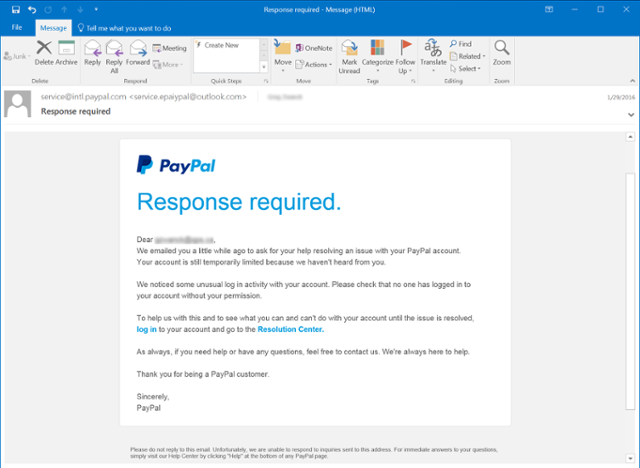
Looks pretty legit. But those links take you to a fake Paypal login page.
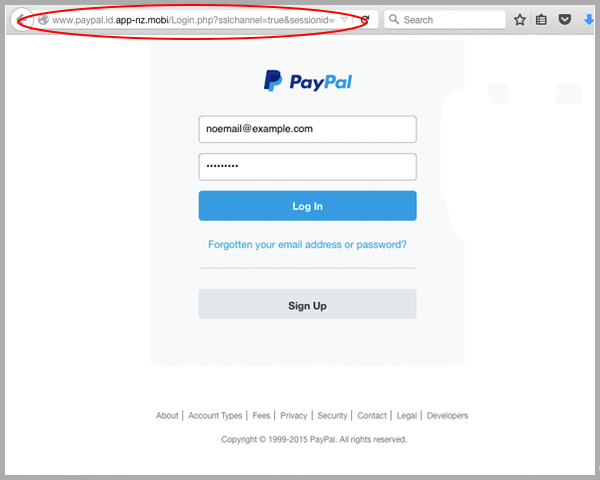
Note the domain name above. It’s very easy to create a fake login page, and harvest credentials from anyone who clicks a link.
This is the basic phishing attack, but there’s a ton of variations on it. Sometimes the phone numbers in the emails are fake, and lead to someone who sounds legitimate, but is trying to get credentials, SSN’s, or other private information. Other attacks are to get email credentials, so that your domain’s email accounts can be used to send even more phishing attacks.
There’s lots of expensive ways to try and prevent this from happening. Some email security providers will hook into your email and filter these out. But they cost a lot of money, and all eventually let some emails through (Google Apps already does filter these, and is pretty good at it).
The most effective solution is also the cheapest. With two factor authentication, even if a user has their credentials stolen, they still can’t be used by a bad actor. The thief needs a unique code to be able to log in and use them and that’s usually provided by the user’s phone. Backstop ensures that your users on Google Apps have enabled two factor auth, and that’s usually the most important account.
You still want to know when a user’s password has been stolen, and most users reuse passwords across different sites. That’s why we also offer breach detection, with instant notification so you can force a password change when necessary. We can even automate that process for you, just let us know. Sign up here.
